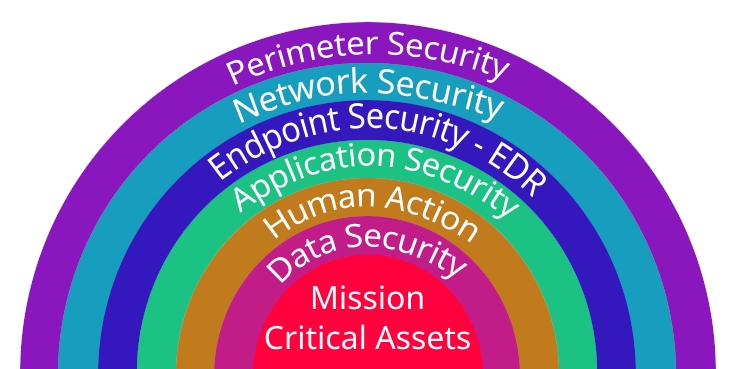
The layers of cyber security defense can be organized into a comprehensive strategy to protect an organization’s information systems and data. These layers work together to create a defense-in-depth approach, acknowledging that no single solution can provide complete security. Here are the key layers of cyber security defense:
Perimeter Security
Behavior monitoring detects and alerts you to any suspicious activity using Intrusion Prevention Services (IPS), Intrusion Detection Services (IDS), Email filtering protection and Next-Generation Firewall Services such as Watchguard Fireboxes.
Network Security
Rules and configurations to secure accessibility and integrity. Generations offers Site-to-Site Connections, Web Content Filtering, Remote Services, and VPN Services.
Endpoint Security
Get real-time protection with Multi-Factor Authentication (MFA), Endpoint Detection and Response, Patch Management, and Antivirus Services where EDR is not used.
Application Security
Every time you deploy new application features or update existing ones, your security measures need to adapt. Vulnerability Scanning and Application Safe listing help secure your applications.
Human Action
Employees are critical when warding off attacks, even though this graphic does not show it that way. Continually educate and train your entire staff with the help of Generation Technology Solutions. Password Management is a great addition for your Employees that are accessing websites and need to keep track of those passwords securely.
Data Security
Data encryption (at rest, in transit), data classification, and data loss prevention which includes Backup and Disaster Recovery, these are services Generations offers to help keep your most valuable asset safe – your data.
Critical Assets
Data (at rest, in transit) and applications, Cloud products and services, all need to have the above listed protections in place in order to be confident your data will not leave your control.
Policy Management: Manage the rules and procedures everyone must follow when accessing and using your IT assets and resources with Access Control, Data Protection, Encryption, and Remote Access Rules.
Monitoring and Response: It is critical to monitor, detect, contain, and remediate attacks. Through tools like File Integrity, IT Service Management, Security Operation Center (SOC), Identity Access Management, Security Information and Event Management (SIEM), and Managed Detection and Response.
Conclusion
These layers collectively provide a robust defense against a wide range of cyber threats. Regular updates, monitoring, and employee education are crucial to maintaining an effective cyber security posture. Keep in mind that the cybersecurity landscape is dynamic, and organizations need to adapt their defense strategies to address evolving threats.
Give us a call today @ 780-413-9908 to discuss how we can decrease your cyber security risk and help your company succeed in today’s evolving threat landscape.